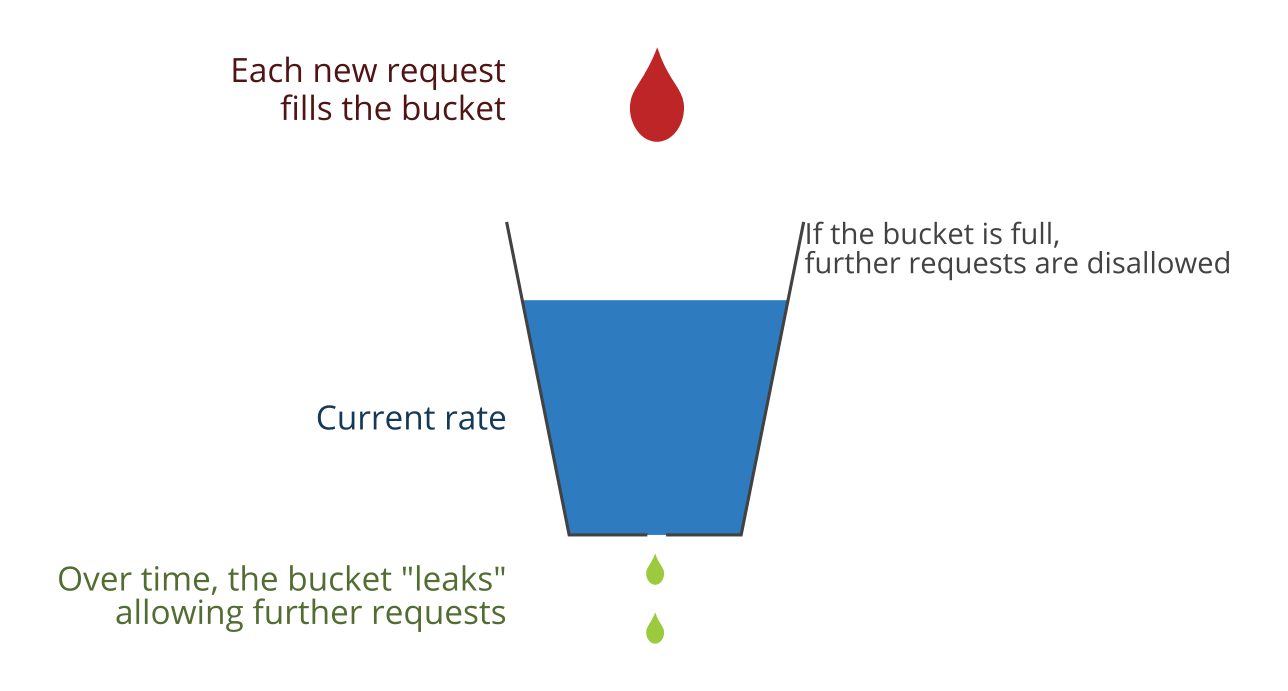
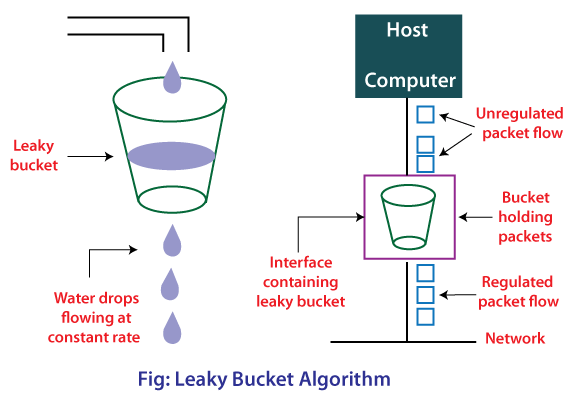
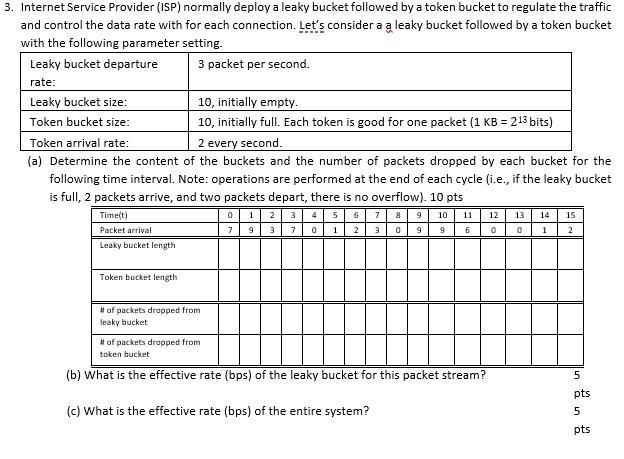
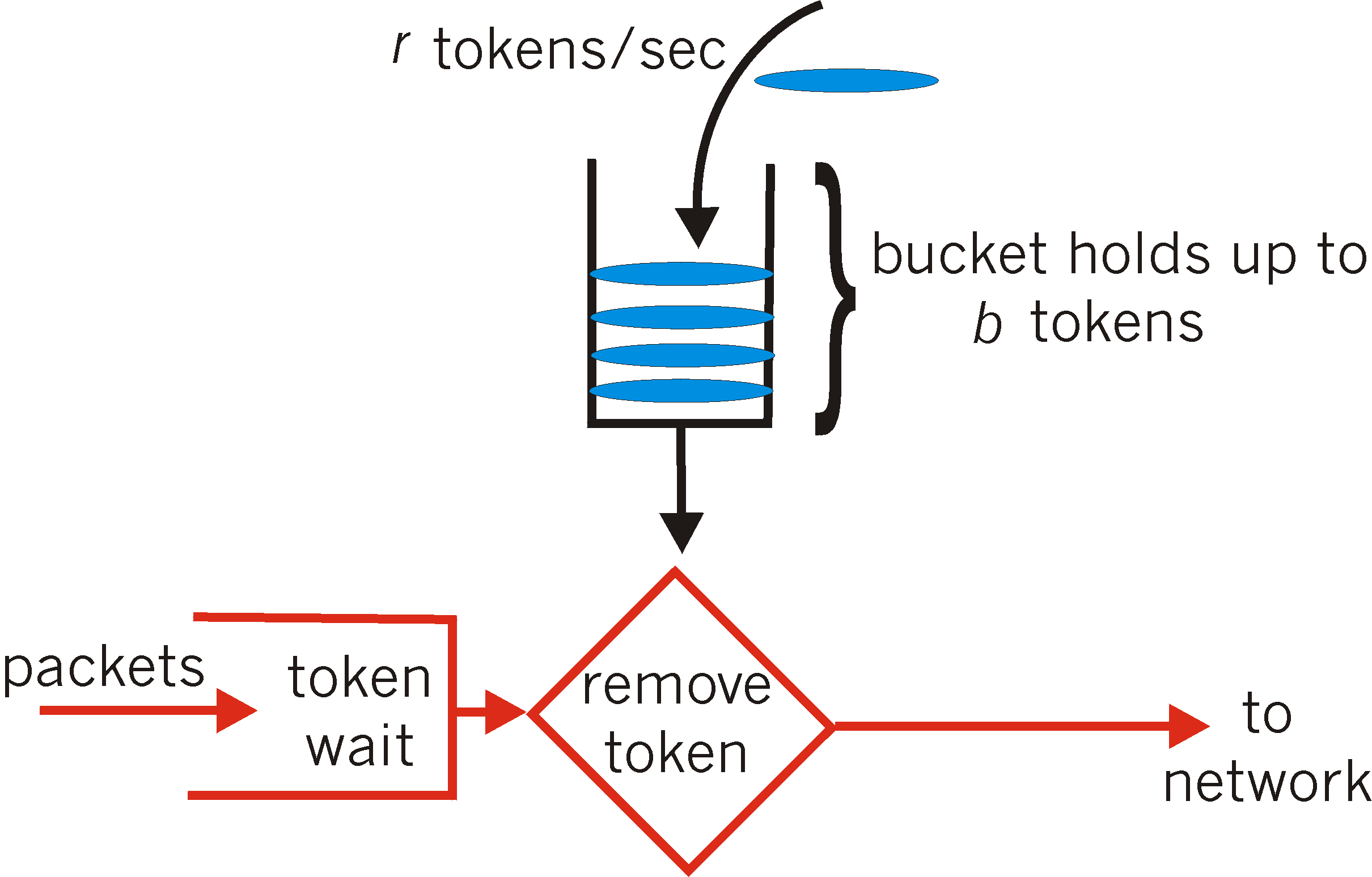
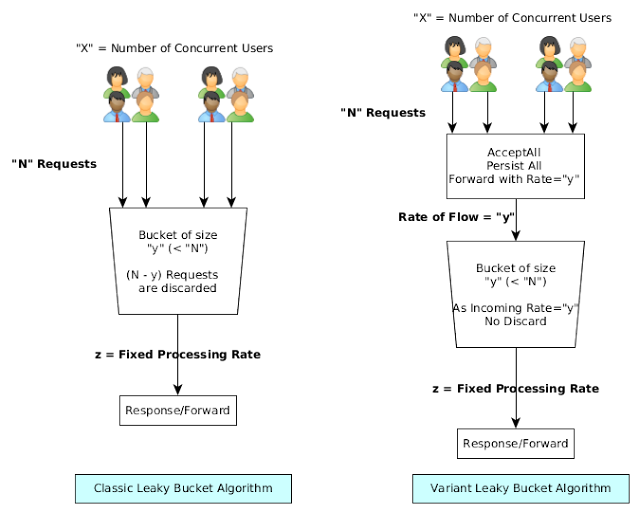
Token Bucket Algorithm In contrast to the leaky bucket, the Token Bucket (TB) algorithm, allows the output rate to vary, depending o.… | Algorithm, Token, Bucket

Security basics: DDoS attacks. No network is safe from hackers these… | by Amar | Internshala Tech | Medium